Achieve Resilient and Comprehensive Automotive Cybersecurity
By Mike Hodge, Product and Solutions Marketing
Key takeaways:
- Automakers have to grapple with vehicle cybersecurity threats emerging from rapid technical advancements as well as decade-old legacy systems.
- The regulatory burden of cybersecurity on the automotive industry is constantly increasing worldwide.
- Automated cybersecurity testing that can seamlessly span complex hardware and software systems is essential.
Most road vehicles were largely mechanical machines with a few electronic systems until just a decade or two ago. But modern vehicles involve so many more computing and software systems that they've been called “software-defined vehicles” and “smartphones on wheels.”
In this article, learn why automotive cybersecurity has become critical, what regulations and standards are in play, and how automakers can effectively implement cybersecurity.
What is automotive cybersecurity?
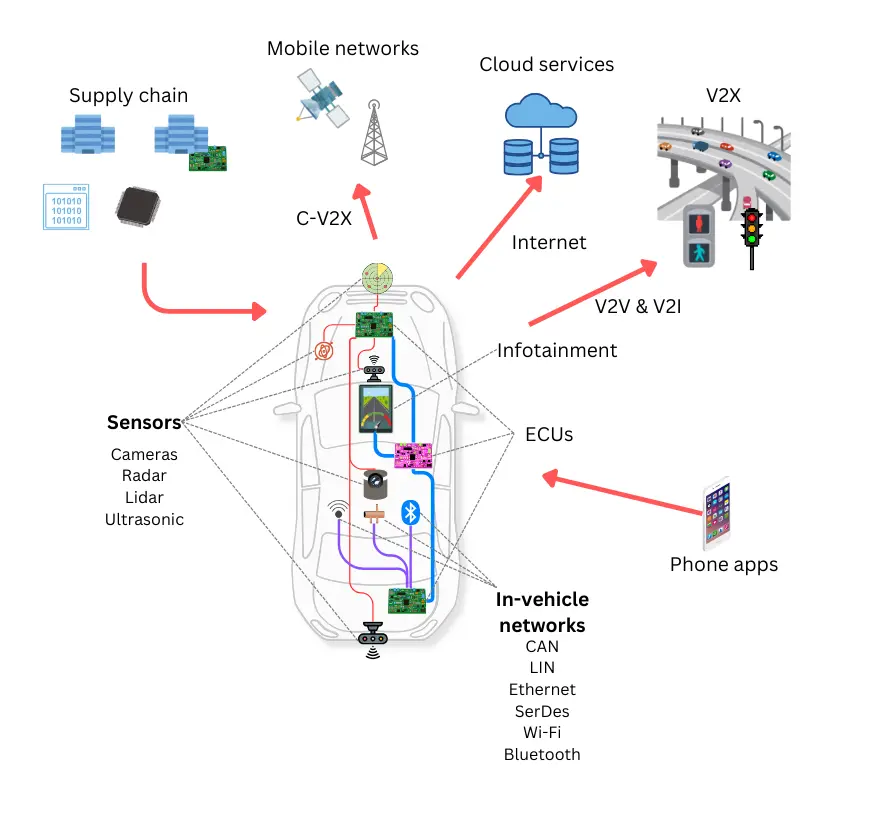
Automotive cybersecurity involves the protection of all the information technology systems related to road vehicles from cyber threats. It includes the cybersecurity of onboard systems as well as external interfaces.
Onboard systems include sensors, electronic control units (ECUs), network chips, embedded systems, and their software.
External systems include vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I), vehicle-to-everything (V2X), and cloud services.
Automotive cybersecurity is a key component of overall vehicle security along with physical security.
Why is automotive cybersecurity critical for modern vehicles?
Automotive cybersecurity has become critical because the computing, software, and connectivity components in vehicles are constantly increasing in number and complexity. Security issues in these components can lead to major problems like:
- Compromised vehicle safety: Most vehicles today are drive-by-wire systems capable of cruise control and even near-autonomous driving. Any malicious actions against such systems can result in catastrophic collisions and fatalities to vehicle occupants, bystanders, and other road users.
- Regulatory compliance failures: Due to the safety-critical nature of vehicles, countries around the world mandate several vehicle safety regulations. Breaching them can result in heavy financial and legal penalties for automakers.
- Damaged reputations: Unsafe vehicles can lead to damaged reputations, loss of market share, and possibly even permanent loss of business for automakers.
What are the common cybersecurity threats faced by connected vehicles?
Some common automotive cyber threats include:
- Remote hijacking: Attackers can take control over critical vehicle functions like steering, brakes, and acceleration by compromising the vehicle’s internal systems through various connectivity interfaces. Typically, this involves unauthorized access to ECUs of vehicles.
- Ransomware attacks: Cybercriminals may implement ransomware to lock the vehicle's systems until a ransom is paid.
- Denial-of-service attacks: Attackers may disrupt the functioning of vehicular systems, rendering them inoperable or causing them to malfunction.
- Data theft: This includes unauthorized access to sensitive data stored in the vehicle, like payment information and personal data. Information security theft and data breaches are probably the most common types of automotive cyberattacks.
- Supply chain attacks: Malicious firmware or software updates can introduce vulnerabilities when the code is deployed to vehicles, compromising their security long after manufacturing.
- Compromised physical security: Hardware attacks against locking mechanisms like key fobs or onboard diagnostics (OBD II) ports can allow physical access to vehicles and open up possibilities of theft, sabotage, or malware injection.
- Attacks on artificial intelligence (AI) models: Advanced driver-assistance systems (ADAS) and autonomous driving systems rely on AI models for image understanding, sensor understanding, and vehicle control. Carefully crafted malicious inputs to these models can give anomalous outputs that result in collisions and fatalities.
- Attacks on electric vehicle (EV) subsystems: EVs have dangerously high voltages and currents around their battery management systems. Any compromises with those ECUs can result in fires, explosions, and similar catastrophes.
What are some important regulations related to automotive cybersecurity?
Among the most important regulations in recent times are the R155 and R156 mandated by the United Nations Economic Commission for Europe (UNECE) World Forum for Harmonization of Vehicle Regulations (WP.29).
These regulations apply to all of Europe, Japan, Australia, and New Zealand, among others. Despite that, most automakers around the world are conforming to them, making them de facto global regulations.
Although they don't place direct obligations on component suppliers, they do so indirectly through requirements on the original equipment manufacturers (OEMs) of vehicles.
These regulations are driving the adoption of automotive standards specified by the International Organization for Standardization (ISO) and the Society of Automotive Engineers (SAE). One such critical standard is the ISO/SAE 21434road vehiclescybersecurity engineering standards.
The two regulations are summarized below.
R155 regulation
R155 mandates a cybersecurity management system (CSMS) and several vehicle-type-specific cybersecurity technical requirements for automakers.
The CSMS establishes a system for cybersecurity governance, risk management, and risk assessments throughout the development, production, and maintenance phases of vehicles. Automakers must get their processes audited annually.
In addition, there are cybersecurity requirements for each vehicle type.
R156 regulation
R156 requires secure and safe software update processes to be established. Automakers must show evidence that their processes don't compromise vehicle safety or security.
How do automotive cybersecurity standards impact vehicle development?
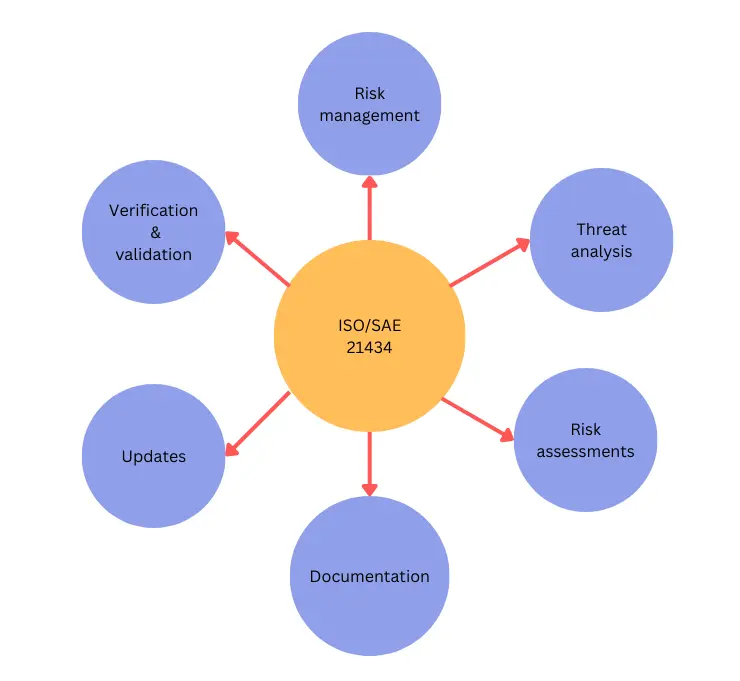
Standards like the ISO/SAE 21434 specify a cybersecurity risk management process that applies to the entire duration of a vehicle, including all its components and interfaces.
This ISO 21434 involves:
- threat analysis and risk assessments (TARAs) to identify and assess cyber risks to their vehicles
- verification and validation testing to ensure that their security mitigations are functioning as intended
- security of all communication interfaces
- documentation of all cybersecurity information like the results of TARAs, verification tests, and incident responses
- continuous monitoring of threats and regular updates
How can automotive cybersecurity be integrated into the vehicle development lifecycle?
Cybersecurity is integrated into the development lifecycle through the following steps:
- Establish cybersecurity governance: Set up a cybersecurity management system and cybersecurity framework.
- Conduct TARAs: Identify threats and risks during the design phase and ensure suitable mitigations.
- Integrate cybersecurity into the V-model: During the design phase, integrate measures to prevent attacks. During the verification and validation phases, confirm those measures through testing and ensure they remain effective throughout the product lifecycle.
- Conduct cybersecurity testing of updates: Ensure that over-the-air (OTA) updates are safe and secure.
- Test continuously: Implement regression and functional testing to ensure security against new threats as they emerge.
- Automate all tests: Automate all this testing through platforms that seamlessly integrate with the multitude of hardware and software interfaces.
- Incorporate threat intelligence: Integrate with real-time threat and vulnerability alert services.
- Mitigate supply chain risks: Ensure that all vendors and suppliers comply with cybersecurity standards as breaches can propagate through the supply chain.
- Document all steps: Maintain comprehensive documentation of all design decisions, test results, and compliance measures.
What are some commonly used automotive cybersecurity testing techniques?
The common testing techniques used are:
- Vulnerability testing: It identifies weaknesses in the vehicle's ECUs, sensors, network chips, and embedded software that could be exploited by malicious actors.
- Penetration testing: Ethical hackers attempt to gain unauthorized access through social engineering and by exploiting vulnerabilities. This simulates real-world attacks by malicious actors.
- Fuzz testing: Fuzz testing uses deliberately malformed inputs to various subsystems to discover unexpected dangerous behaviors and observe the vehicle's resilience against them. The inputs are sent via communication packets or other interfaces to the hardware and software used in the vehicle. It can discover flaws that could lead to security breaches.
- Regression testing: This ensures that existing security measures remain effective for the vehicle's lifetime after every change or update.
How are automotive cybersecurity vulnerabilities identified and mitigated during testing?
The attack chains that expose vulnerabilities can vary widely in complexity and depth.
Some vulnerabilities may be easily discoverable by studying the circuits, software code, datasheets, or manuals and observing their behaviors. Such surface-level vulnerabilities can be identified and mitigated through TARAs and vulnerability testing.
However, other serious vulnerabilities may lie much deeper than that. They may involve complex attack chains that span multiple hardware and software systems. They may emerge from seemingly innocent inconspicuous backend interactions between systems. Only experienced cybersecurity specialists can identify them using techniques like penetration and fuzz testing.
All vulnerabilities are mitigated as described below.
- Designing mitigations: Automakers design mitigations to address vulnerabilities through secure software implementations, access controls, and encryption protocols.
- Verification and validation testing: After implementing security countermeasures for detected vulnerabilities, rigorous testing is conducted to validate their effectiveness. Verification and validation testing (V&V) ensures that the designed mitigations are functioning correctly.
- Automated regression tests: Automated regression tests can be run whenever there is a software update or new vulnerabilities are discovered. This ensures that all existing mitigations remain effective over time.
- Periodic audits: Regular audits are conducted to ensure that the security measures remain adequate and effective against emerging threats. Automakers must maintain a cycle of continuous improvement that incorporates lessons learned from both testing and real-world incidents
What are some cybersecurity best practices for protecting in-vehicle and vehicle-to-everything (V2X) networks?
In-vehicle networks — like the controller area network (CAN), local interconnect network (LIN), and automotive Ethernet — and outfacing networks like V2X are often the vectors of choice for many cyberattacks. Some best practices from the National Highway Traffic Safety Administration (NHTSA) and other agencies are outlined below:
- Design for security: Security should be integrated into the vehicle right from the design phase. All potential attack surfaces must be identified and mitigated early.
- Defense in depth: Implement strict access controls and encryption. Critical functions like braking and steering must not be accessible through less secure components like infotainment systems.
- Protocol fuzz testing: Conduct protocol fuzz testing to identify vulnerabilities at lower communication levels. This can uncover weaknesses in embedded chipsets and communication protocols.
- Penetration testing: All protocols tend to have some undefined behaviors in their specifications. A best practice then is to have penetration testing done by experienced red teams proficient in the intricacies of in-vehicle network protocol specifications.
- Threat intelligence: The testing should be integrated with threat intelligence services to anticipate and respond to emerging cyber threats.
How do over-the-air (OTA) software updates affect automotive cybersecurity?
Some potential security problems due to OTA updates include:
- Insecure code in the updates: Vulnerabilities may creep in inadvertently due to feature updates that focus on functionality while forgetting security aspects. These typically result in reduced security, but catastrophic outcomes are rare.
- Malicious updates from rogue sources: In such attacks, the vehicle's subsystems receive malicious updates that open up new vulnerabilities or cause catastrophic failures. This is achieved either by manipulating the update sources on the vehicle or taking over the manufacturer's update servers.
- Faulty update steps: Faulty update steps may result in reduced security or even catastrophic outcomes.
To mitigate such issues, automakers must implement the techniques outlined below:
- Digital signatures: The updates must be digitally signed using cryptography keys that are already known to the vehicle.
- Dual image fallback: Every onboard system must support dual image architecture and partitions.
- Automated testing of updates: Every update must undergo functional, regression, and fuzz cybersecurity tests. For major updates, penetration testing is also recommended.
What are the challenges of automotive cybersecurity testing?
Some key challenges are outlined below:
- Expanding attack surface: The number of complex hardware and software systems keeps increasing as vehicles become more interconnected. The number of attack vectors and attack paths is also constantly increasing.
- Evolving threat landscape: Rapid technical advancements like automotive radars and AI keep adding new vulnerabilities and potential threats.
- Supply chain vulnerabilities: The potential for vulnerabilities in the supply chain also increases. Cybercriminals can exploit weaknesses in third-party vendors' systems and processes.
- Long lifetimes: A typical vehicle's lifetime is a decade or more. Automotive cybersecurity must not only keep up with new threats but also ensure that the legacy parts don't become insecure.
- Regulatory compliance: Automakers must adhere to stringent safety and security regulations.
- Organizational challenges: Continuous testing requires skilled personnel and significant financial resources. Many automakers struggle to maintain the necessary level of cybersecurity expertise within their teams for a vehicle's lifetime.
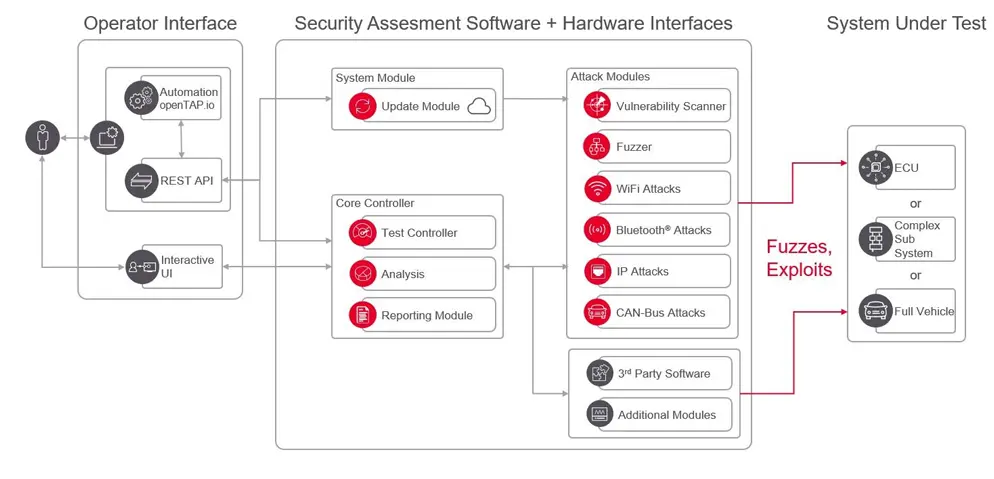
How does the Keysight SA8710A platform address automotive cybersecurity challenges?
The Keysight SA8710A is a comprehensive platform to address the above automotive cybersecurity challenges. Its key features are outlined below.
Modularity
The platform's hardware and software modularity enables plugin support for multiple communications including cellular (2G, 3G, 4G, and 5G), cellular V2X, CAN bus, automotive Ethernet, Bluetooth, and Wi-Fi. Automakers can manage both expanding attack surfaces and emerging threat landscapes.
Automated cybersecurity testing
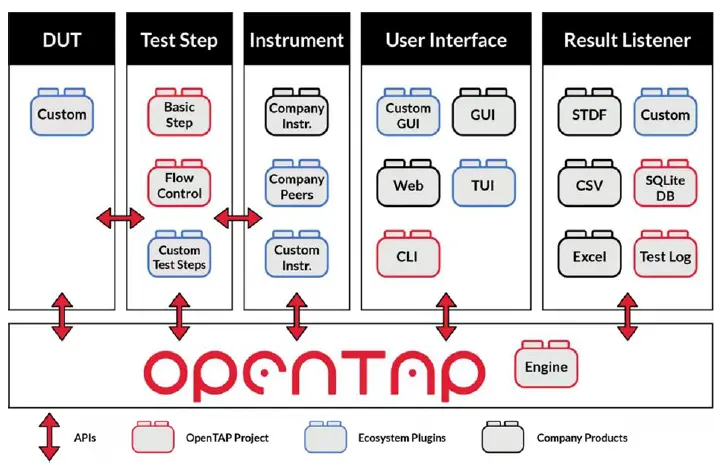
The most striking feature is its ability to automate entire attack sequences, fuzz testing, penetration testing, and vulnerability assessments using the built-in open test automation platform (OpenTAP) engine, test sequencer, and plugins.
Built-in regulatory compliance
The platform enables automakers to comply with R155 regulations.
Threat intelligence
The platform includes an application and threat intelligence subscription.
Documentation
The SA8710A can generate all the required documentation required by regulations like R155 during audits. This includes test plans and results that are integral to an OEM's CSMS.
What does the SA8710A automotive cybersecurity platform consist of?
The SA8710A consists of the following software components:
- PathWave test automation platform
- OpenTAP engine
- Penetration testing software
- Attack modules for various communication protocols
- Plugins for automated test steps
- Plugins for connecting to instruments and devices under test
- Fuzzer plugins like the CycurFUZZ
The hardware components include:
Get comprehensive automotive cybersecurity testing from Keysight
Keysight's automotive networking and cybersecurity solutions enable comprehensive security testing of all vehicle subsystems at all levels.
Our team of highly experienced cybersecurity professionals also provide expert services for UN R155 and UN R156 vehicle type approvals. With in-depth expertise in these regulations and state-of-the-art technologies for cybersecurity testing, they ensure that your compliance is in the best hands.
Contact us for insights and recommendations on keeping on top of your automotive security challenges.