Cyber Threats to Physical Assets Demand a Proactive Approach
Government and utility leaders understand the importance of maintaining security across IT, OT networks
Intent on safeguarding the nation’s largest electric grids from potential mayhem, federal regulators have stepped up their oversight of the security of power utilities in an attempt to protect it from threats and incidents such as widespread, long-duration blackouts caused by digital saboteurs. Cyber threats linger, however, with operational technology (OT), including water systems that are far less centralized and, thus, more vulnerable.
As efficiency efforts drive IT and OT systems to converge, hackers can gain access to the OT infrastructure via an IT route, fueling a need for utility leaders to assess, plan and implement OT protection strategies for critical assets. This position represents a fundamental shift in approach whereas security, once set up under IT only or as a separate shop, is being integrated into a broader IT/OT function.
Download the 2018 Smart Cities & Utilities Report
The U.S. Department of Homeland Security has labeled cyber attacks on critical infrastructure among the nation’s most serious security challenges. Not unexpectedly, government and utility leaders clearly understand the importance of maintaining security across IT and OT networks.
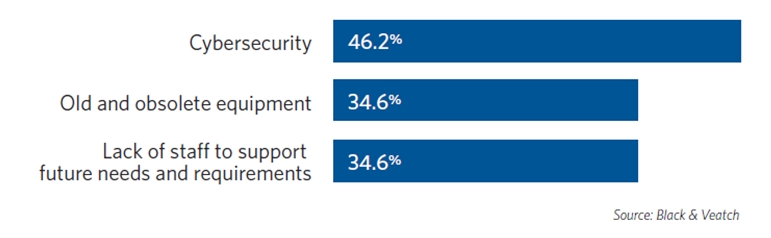
When asked to select the top three major challenges with their current distribution system automation and communication capabilities, nearly half of survey respondents cited cybersecurity; old and obsolete equipment and a lack of staff to support future needs and requirements tied for second, each with 35 percent (Figure 1).
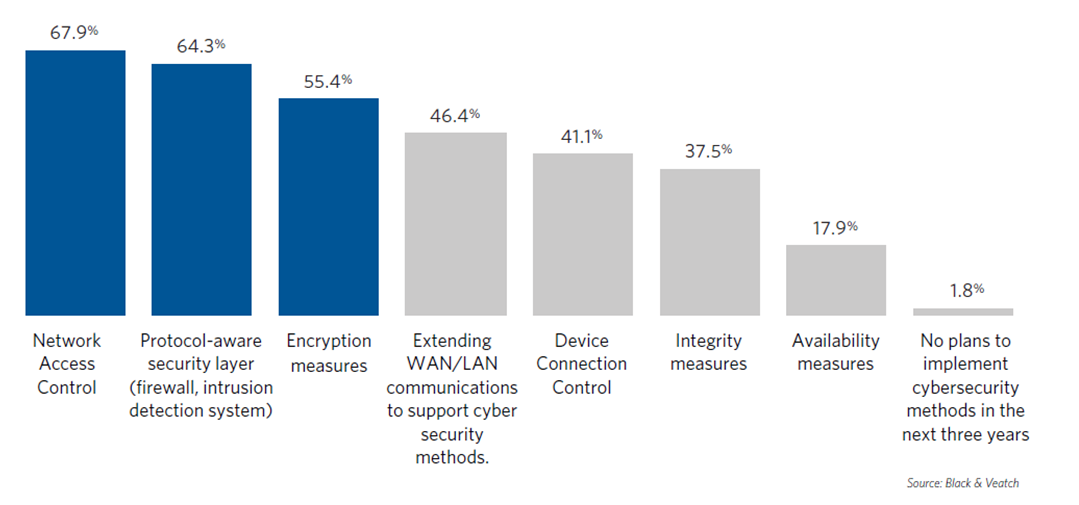
When asked separately where cybersecurity measures will be implemented in their networks within the next three years, 64 percent of respondents cited addressing any shortcomings in their core assets as their top priority. Edge assets such as switches, regulators and capacitor banks were ranked second (43 percent) and backhaul third (34 percent). However, addressing core vulnerabilities may be the quickest, easiest response and can more easily leverage in-house resource capabilities because of its relatively small scale. Focusing on physical assets may prove to be more complex, given the larger scale and the fact that many infrastructure assets were designed and built years ago without security in mind and at a time when the prevalence of analog systems brought security through technological obscurity. In recent years, sophisticated rogue actors have brought the need for upgraded system defenses to the fore, making the threat more than simply theoretical. In 2011, the Stuxnet computer virus reportedly destroyed centrifuges involved in Iran’s nuclear program. In 2013, Iranian hackers breached the command-and-control system of a dam near Rye Brook, New York, managing to gain access to the floodgates — a breach Sen. Charles Schumer of New York called “a shot across our bow.” In September of last year, according to The Associated Press, cybersecurity firm FireEye warned that a group of hackers suspected of working for the Iranian government was targeting the aviation and petrochemical industries in the United States, Saudi Arabia and South Korea. Across the digital landscape, threats are limited only by the imagination and deviousness of those carrying out cyber mayhem. Video surveillance cameras and wireless routers also may be vulnerable to online intruders, cybersecurity experts have warned. Cyber threats are gaining the attention of U.S. industry leaders. According to the 2018 Strategic Directions: Smart Cities & Utilities Report survey, more than 60 percent of respondents cited upgrades in network access control and in firewalls and intrusion-detection systems — all relatively simplistic doors to close — as cybersecurity methods they plan to adopt within the next three years. More than half said they expect to deploy encryption techniques (Figure 2). Rapid evolution of electric grids and communications networks can make it difficult to plan safeguards, but asset managers must assess their risks and adopt responsible security measures that are flexible and scalable, shunning dismissive attitudes that such investments simply become outdated within a few years. A truism of cybersecurity is that the risk level is never zero. The quest for brawnier security begins with a deep-dive assessment of critical infrastructure to understand the networks, cyber asset inventories and existing risks, then deciding what risks are acceptable and which to remediate. By quantifying risk, stakeholders can prioritize and justify investments in cyber protection to maintain an acceptable level of risk and a sustainable security posture.