Utilities Must Constantly Be on Offense in Cat-and-Mouse Game Against Hackers
Facing increased risk by hackers, utilities are ramping up cybersecurity
For power suppliers wanting to be vigilant about the threat that hackers pose to the grid, a March 2019 intrusion may have been a benign warning about vulnerability. When hackers disabled a Utah-based renewable energy developer’s control system for about a dozen solar and wind farms in the West, the grid’s operators were left blinded for more than 10 hours to those 500 megawatts of generation sites. Thankfully, no outages resulted.
It was the latest salvo in an evolving but unceasing chess match between U.S. utilities and the mischief-minded who are eager to disrupt, using a keyboard as their weapon. Each is trying to think two moves ahead of the other, with utilities disadvantaged by the fact that the rules keep changing.
With the influx of distributed energy resources (DER), power grid and communications networks are becoming more integrated and complex, uniquely challenging utilities and widening their exposure to those seeking to maliciously exploit them, or simply disrupt them. The industry’s embrace of internet-connected sensors — in short, digital transformation — expands its vulnerability through a much broader “attack surface.”
Without question, utilities understand the risks and have staved off sizable disruptions, in part thanks to the North American Electric Reliability Corporation’s (NERC) critical infrastructure protection (CIP) guidelines that have proven to be good road maps toward what should be a more proactive, robust and holistic approach to securing critical infrastructure.
As hackers grow more sophisticated, utilities know they must do likewise. Black & Veatch’s 2020 Strategic Directions: Smart Utilities Report survey finds that utilities are embracing the need to enhance their cyber defenses. With the uptrend of adopting cloud computing and packetized Internet Protocol (IP) networks in the operations technology (OT) telecommunications environment, utilities acknowledge that a formal, robust network and security operations center (NOC/SOC) becomes a new common denominator of cyber defense.
This more proactive pursuit of an enhanced monitoring-and-response cybersecurity posture comes as these new IP packet-oriented requirements compete against other legacy considerations, including that pesky thing called aging infrastructure.
Cyber Monitoring: Not Just for the Big Kids Anymore
Faced with the need to modernize, utilities are prioritizing, making it unsurprising that two-thirds of respondents named reliability a major driver in their efforts to upgrade. Roughly four of every 10 survey takers cited quests to bolster operational efficiency, address aging infrastructure and increase monitoring, control and automation. Just 12 percent of respondents said cybersecurity is among their top priorities.
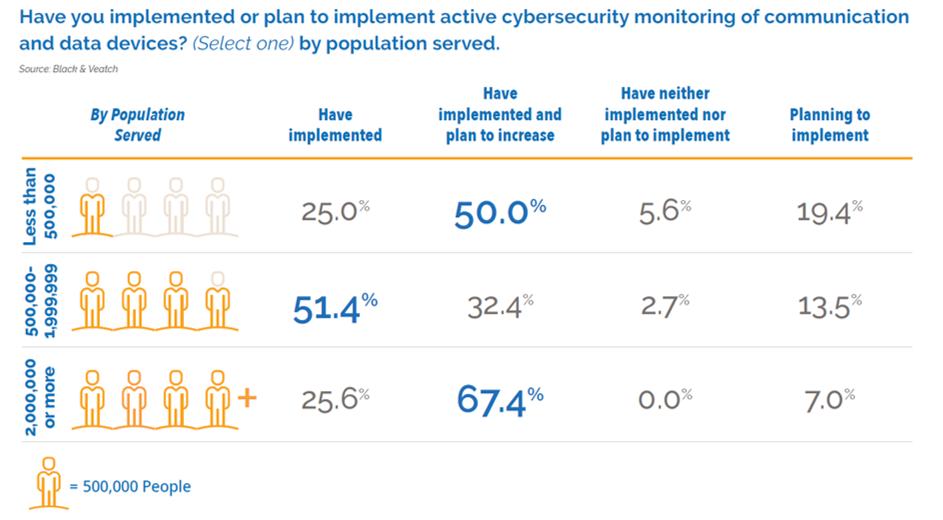
But when asked separately whether they’ve implemented or plan to put into action active cybersecurity monitoring of communications and data devices, eight of every 10 respondents said they either have adopted such measures or have done so with plans to bolster them.
But the good news is that two-thirds of the largest utilities say they expect to increase their cybersecurity safeguards going forward. And most respondents, utilities both big and small, say they have a plan for cyber oversight.
Options for stepping up cyber defenses can take many forms, not the least of which are in-house SOCs dedicated to preventing, detecting and responding to cyber threats and hacking incidents. Such investments — ideally positioned in tandem with, but isolated from, any NOC — help utilities better safeguard their critical infrastructure and highly sensitive operational information. This offers utilities more control over their security monitoring, incident response and communications with regulators and law enforcement entities.
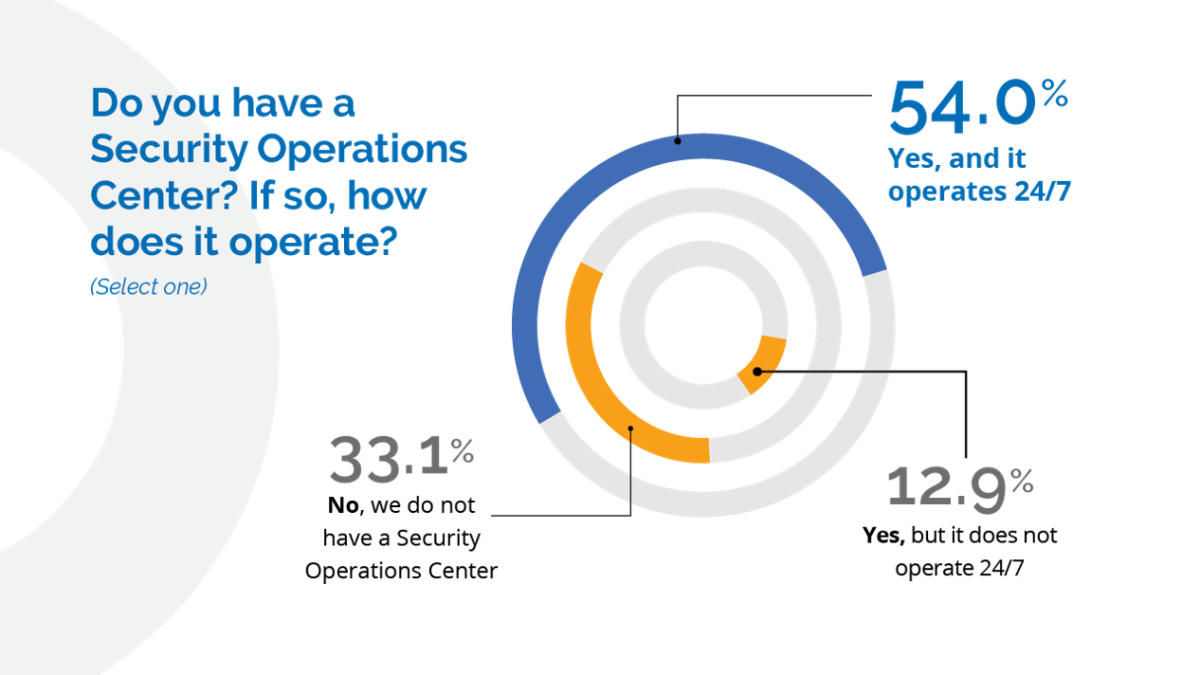
Creating a SOC — or some form of internal security operations capabilities — can be time-consuming and expensive, which often leads to security monitoring being outsourced. In either case, the survey shows that utilities value the concept, with more than half of respondents saying they have turned to that measure and it operates around the clock.
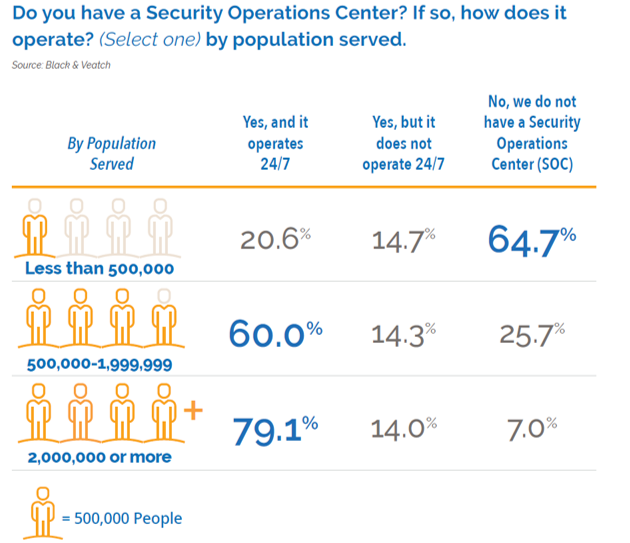
Utilities serving populations of more than 500,000 are overwhelmingly the ones with SOCs that work 24/7, perhaps because they’re better equipped to fund them, and they exist in areas where more qualified resources are available.
While such responses are commendable, none of them reflect the extent to which each of those SOCs is truly effective, or whether they have shortcomings. Are there multiple dedicated, full-time people assigned to that cybersecurity role? Are they fully qualified? Is that worker regularly reviewing logs? Is there intrusion monitoring and detecting?
Another thing to ask: Why do one-third of respondents have no SOC at all?
Perhaps it’s simply a matter of budget, given that nearly two- thirds of respondents at the nation’s smaller utilities (which serve fewer than 500,000 residents) say a SOC isn’t part of their game plan. There also may be some connection with smaller electric utilities having fewer NERC-CIP-rated “high” and “medium” assets and systems.
Among Utilities, Cloud Demand Is Looking Up
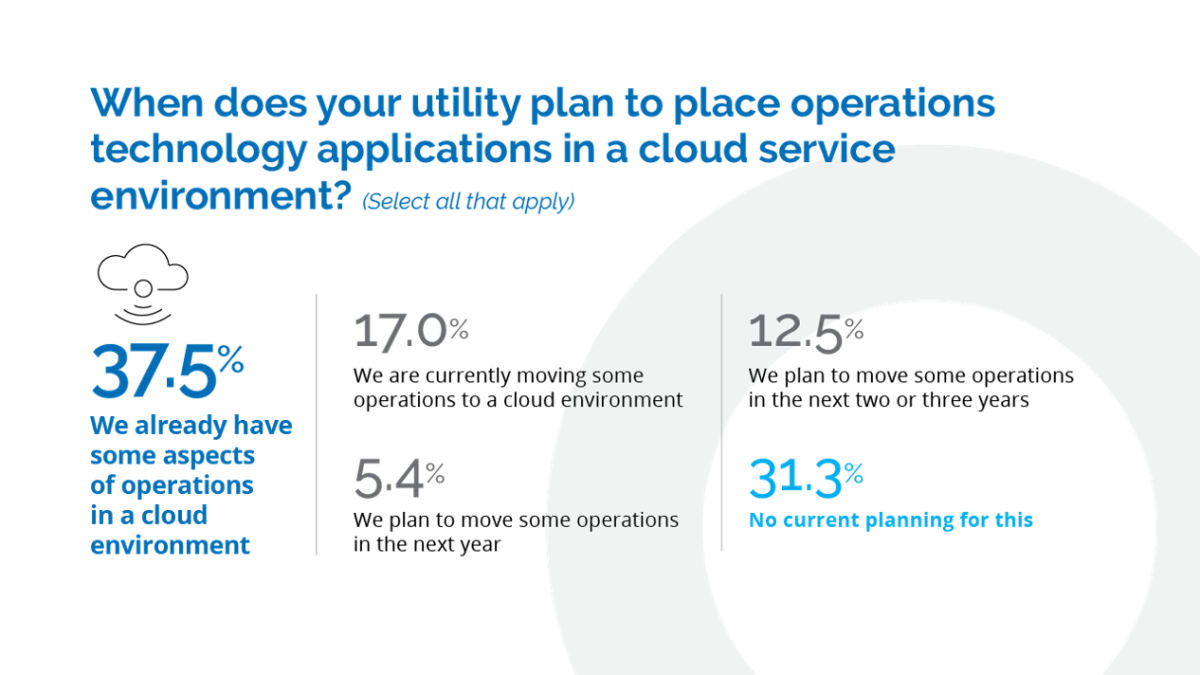
Black & Veatch’s survey shows that more and more utilities are applying concerns to cloud computing as they work to get sensitive information off-premises in a secure manner, store it protectively while the data is at rest and control access while it
is off-site. More than half of the respondents say they’ve already moved or are in the process of moving some operations to the cloud, while nearly one-third say they’re content staying on the sidelines (Figure 33).
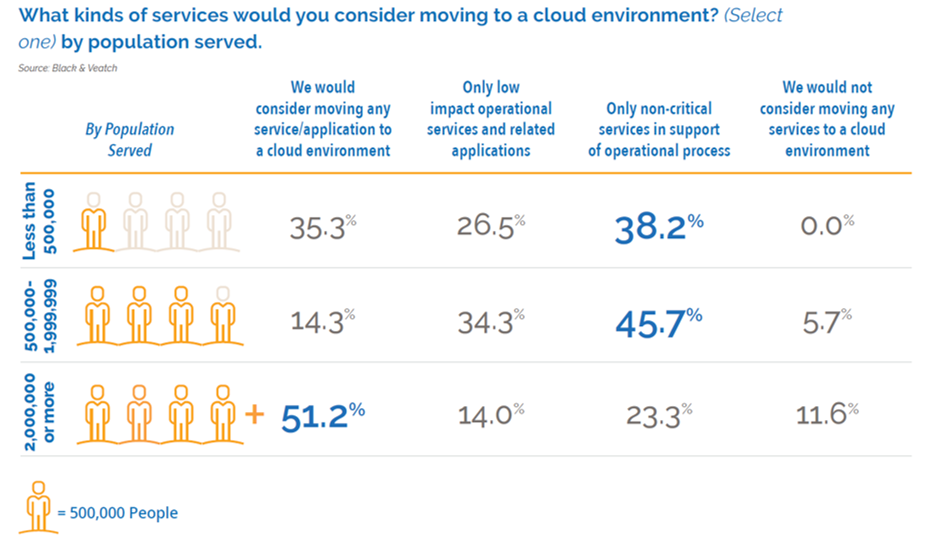
But exactly what utilities feel comfortable storing in the cloud depends on who you ask. More than half of respondents from utilities serving at least 2 million residents say they’d consider moving any service or application to a cloud environment, while four of five respondents from utilities covering populations of 500,000 to 2 million say they only would consider cloud services for NERC-CIP low-impact or noncritical services (Figure 34).
Whatever the case, utilities benefit by having fuller awareness of what storing potentially sensitive data about their electric grids in the cloud may create in terms of additional vulnerabilities and associated business risk. Cloud-using utilities that don’t meet NERC-CIP requirements for encryption — in transit and at rest may face greater exposure and higher risk and, by extension, the potential for punishing regulatory fines.
Best Cyber Posture: Keep Moving the Ball Downfield
As the cyber landscape grows more complex and treacherous, utilities don’t have the luxury of standing pat. They shouldn’t hesitate to consult trusted advisors with tested telecommunications experience to quickly but thoughtfully develop, shore up or expand their risk-management approaches, which should include layered defenses, enhanced monitoring and reliable system redundancies.
The bottom line is that simply sustaining the status quo should be as much of an enemy as hackers themselves; cyber defenses must be flexible and match the pace of digital change.
“Whatever the issue, we all must be clear-eyed about cybersecurity threats and not rest on our laurels,” Neil Chatterjee, the Federal Energy Regulatory Commission’s chairman, wrote in an October 2019 guest column for Fortune. “The electric grid is far more secure than it was a decade ago. But know this: Our adversaries will not rest. Neither can we.”